Why Are Strings Immutable in Java? Discovering the Style Decisions
Why Are Strings Immutable in Java? Discovering the Style Decisions
Blog Article
The Advancement of Immutable String Handling: A Crucial Facet of Software Application Growth
In the complex realm of software application development, the handling of unalterable strings stands as a cornerstone that has undertaken significant development over time. From its humble origins to the facility challenges come across in early executions, the trip of immutable string manipulation has been an essential aspect of software application design. As we navigate through the historic landscape of this essential principle, mapping the developments, security implications, and emerging fads, we locate ourselves at a juncture where the intrinsic worth of recognizing this evolution comes to be increasingly obvious.
Origins of Immutable Strings
When designers sought to boost the dependability and safety and security of data dealing with systems,The idea of immutable strings traces back to the very early days of shows languages. Unalterable strings describe strings that can not be changed after they are created. This basic concept was introduced to address issues concerning data honesty and stop unexpected modifications to important information kept as strings.

Additionally, immutable strings add to enhancing the total safety and security of software systems (Why are strings immutable in Java?). By stopping unauthorized events from damaging delicate string information, unalterable strings help mitigate the threat of information violations and unapproved access to confidential info. This foundational idea remains to play a crucial duty in modern programming languages and stays a keystone of safe and secure and robust software program advancement techniques
Very Early Challenges and Solutions
Browsing the landscape of very early software development presented considerable difficulties in making sure the honesty and safety of data taking care of mechanisms. One of the primary challenges in dealing with immutable strings was taking care of memory successfully. In early systems, memory appropriation and deallocation were manual processes, causing possible memory leakages and vulnerabilities. In addition, ensuring that strings stayed unaltered proved to be complex, specifically when numerous parts of the codebase needed to gain access to and customize information.
To attend to these challenges, developers began executing information encryption strategies to protect sensitive details stored in immutable strings. By including security and hashing techniques right into the handling of immutable strings, designers substantially boosted the safety and dependability of information within software program systems.
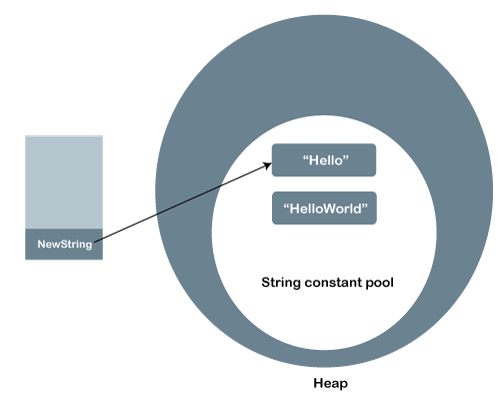
Developments in String Immutability
In software program development, a remarkable evolution in the handling of unalterable strings has emerged via improvements in information security and hashing techniques. By helpful site utilizing secure hash formulas like SHA-256 or cryptographic methods such as AES security, programmers can guarantee that sensitive info stored in immutable strings stays safe and secure and tamper-proof. These innovations have actually reinforced the stability and privacy of information within applications, especially in industries where information safety is extremely important, such as medical care, finance, and cybersecurity.
Additionally, developments in string immutability have actually paved the means for improved performance optimization. Immutable strings allow for much more efficient memory management and caching techniques, minimizing the expenses linked with frequent string manipulations (Why are strings immutable in Java?). This optimization not just enhances the overall responsiveness of software applications however additionally adds to far better scalability and resource application
Safety And Security Implications and Best Practices
With the foundation laid by developments in string immutability, recognizing the safety and security ramifications and carrying out finest techniques becomes critical in protecting sensitive information within software program applications. Unalterable strings play a crucial duty in improving security by avoiding unauthorized modifications to data, guaranteeing information integrity throughout the application's lifecycle. By making use of unalterable strings, designers can mitigate usual vulnerabilities such as injection assaults, buffer overflows, and data tampering, which are commonly manipulated by malicious stars to compromise systems.
This includes encrypting information at rest and in transit, applying appropriate access controls, utilizing secure coding practices, and routinely upgrading software program parts to spot well-known vulnerabilities. By incorporating these protection actions and best techniques into software program development processes, companies can much better safeguard their information possessions and reduce the threat of security violations and data leaks.
Future Fads in String Handling
Amidst the ever-evolving landscape of software program growth, the trajectory of string handling is positioned to witness significant innovations and advancements. Among the vital future patterns in string handling is the enhancing focus on efficiency optimization. As software applications remain to expand in intricacy and range, the effective handling of strings ends up being essential for maintaining ideal efficiency. Programmers are exploring brand-new formulas and data web link structures to enhance the speed and efficiency of string operations.
Moreover, another fad on the perspective is the combination of fabricated intelligence (AI) and artificial intelligence (ML) in string taking care of tasks. AI-powered devices are being established to automate and streamline different string manipulation processes, bring about increased productivity and accuracy in software application development workflows.
In addition, there is a growing focus on enhancing the protection facets of string dealing with with progressed encryption techniques and safe coding practices. As cyber dangers continue to evolve, ensuring the integrity and confidentiality of data within strings is coming to be a top concern for developers. By embracing durable safety measures, such as security at rest and in transit, programmers can minimize the risks associated with string manipulation vulnerabilities.
Final Thought
In conclusion, the evolution of immutable string handling has actually been a critical aspect of software development, starting from its beginnings to the innovations made recently. Early obstacles have web link actually been dealt with through cutting-edge solutions, resulting in improved safety and security techniques in dealing with strings. It is important for designers to remain upgraded on the current fads in string immutability to guarantee the effectiveness and security of their software application applications.
Unalterable strings refer to strings that can not be changed after they are produced. Why are strings immutable in Java?. By preventing unauthorized parties from meddling with sensitive string information, unalterable strings aid mitigate the threat of information breaches and unauthorized accessibility to confidential info. By integrating file encryption and hashing techniques right into the handling of unalterable strings, developers dramatically improved the security and dependability of data within software program systems
Unalterable strings allow for a lot more efficient memory administration and caching methods, reducing the expenses linked with regular string controls. Unalterable strings play an essential role in enhancing safety by protecting against unapproved modifications to information, making sure information stability throughout the application's lifecycle.
Report this page